New types of mobile malware make headlines every day, but what are the most prevalent threats out there? The team at Nominum decided to find out by analyzing Domain Name System (DNS) data of approximately half a million users from various countries.
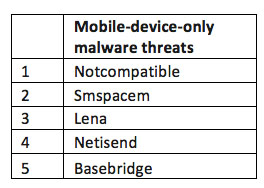
Most malware uses the DNS to communicate and our technology processes about 30% of the worlds’ DNS traffic, so we were able to identify the top five mobile-only malware threats.
 We defined greatest threat as the most widespread malware that meets a baseline level of risk to the end user — for example, malware that attempts to steal a person’s identity and/or money. What follows is a summary of the current mobile malware landscape and a short description of each malware threat, along with some thoughts on what can be done to protect end users.
We defined greatest threat as the most widespread malware that meets a baseline level of risk to the end user — for example, malware that attempts to steal a person’s identity and/or money. What follows is a summary of the current mobile malware landscape and a short description of each malware threat, along with some thoughts on what can be done to protect end users.
But how bad is it, really?
The mobile malware threat is real with a significant number of infections in existence today that are capable of stealing mobile phone users’ identity, and this number is growing everyday. Our research shows that Android remains the top target of malware writers.
Despite that finding, our data was not extensive enough to prove just how prevalent threats were in the U.S. specifically, but recent research has shown that malicious links within text continue to be the biggest concern for mobile device users in the U.S. with 4 in 10 American users likely to click on an unsafe link.
Although Androids topped the list of mobile malware targets, there are still major regional differences in mobile malware prevalence. For instance, “Notcompatible” has a much higher infection rate in Latin America, while “SMSPACEM” and “Netisend” are much more prevalent in the Asia Pacific regions.
These regional differences may be explained by end users’ personal networks. Like a cold or virus in the real world, once someone in a community gets infected with a mobile malware, they are more likely to spread it to others in that community — instead of a sneeze, it is through SMS. As the mobile malware area is less mature than its fixed counterpart, it may take more time for mobile threats to “jump” networks; this will change soon, though, as malware threats get more sophisticated.
Mobile malware writers are leveraging many of the same social engineering techniques (e.g., spreading through end users’ contact lists) and technical capabilities (e.g., rootkits) to spread and make money they’ve used on the Fixed side for years. As the proliferation of smartphones continues and the mobile ad market matures, the incentive of higher profit possibilities will encourage malware writers to write more sophisticated malware.
With multiple mobile operating systems and a vast array of devices, device-based anti-malware software alone isn’t a scalable solution to the problem. The DNS enables a network-based approach for preventing malware that works regardless of what type of device is infected.
The DNS is primarily thought of as a functional technology to navigate the Web, as its original role was to facilitate ease of use of the Internet. DNS eliminates the need to type in long strings of numbers (IP addresses) to access content and translates the numbers into words. Due to its history, DNS has become an often-overlooked layer but it is essential to the network running. As network activity has advanced (think the proliferation of applications, mobile banking, etc.), the DNS layer has evolved into an efficient network infrastructure tool that guides high-performance transactions.
In the case of mobile malware threats, the DNS layer can be analyzed to detect and mitigate suspicious activity. Accordingly, solutions have been invented that enable mobile carriers to layer security applications upon their pre-existing DNS network. These applications can conduct a number of roles from detecting and thwarting hackers’ efforts to alerting users of potentially dangerous mobile websites.
Compared to other solutions, utilizing the DNS layer allows for a faster response time and cost-effective options — both important benefits to a mobile carrier and its subscribers. The DNS’s ability to secure networks should be a part of the modern mobile operator’s security playbook because the mobile malware problem is only going to get worse before it gets better.
Here are the top threats that we’re up against:
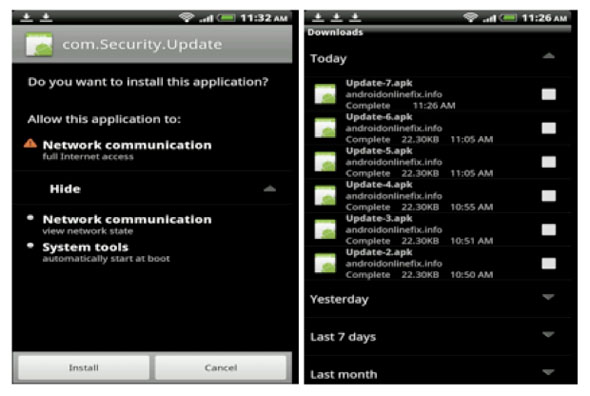
* NOTCOMPATIBLE — The worst of all malware created in 2012 is a drive-by Trojan which can infect Android phones via their mobile Web browsers. When a browser’s download is completed, it will ask for user permission to install as depicted below. After infection, the Android phone can work as a proxy. It is widespread and growing every day. [Also see: “For the first time, hacked websites deliver Android malware”]
* SMSPACEM — This is the second-most widespread malware for Android phones in 2012. It will change a phone’s wallpaper and send anti-Christian jokes by SMS to all the user’s contacts. Here is an example: “Looks like Jesus is a no-show, maybe Judaism was on to something Cannot talk right now, the world is about to end Just saw the four horsemen of the apocalypse and man did they have the worst case of road rage Prepare to meet thy maker, make sure to hedge your bet just in case the Muslims were right.”
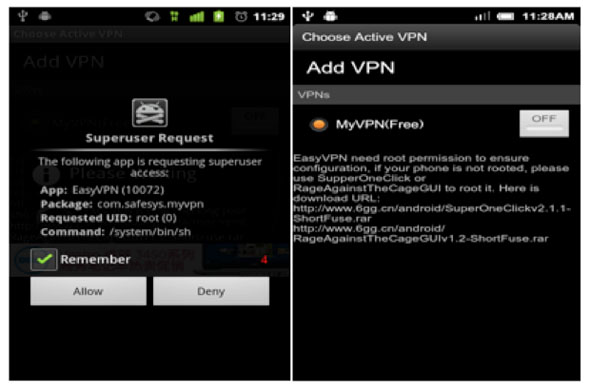
* LENA — This Android-based malware is capable of taking over a user’s phone without asking permission by using an exploit such as gingerbreak or appearing as a VPN app. Once gaining root access, LENA can start to communicate with its command an control site, download additional components and update installed binaries.
* NETISEND — An information stealer on Android phones, it can retrieve information like IMEI, IMSI, model information and installed applications. After downloading, the malware will ask permission to connect to the Internet and open a backdoor with its C&C domain site.
* BASEBRIDGE — It can get an Android phone root access by exploiting netlink message validation local privilege escalation vulnerability. Once infected, Basebridge can disable installed AV software, download additional malware components and open a backdoor with its C&C site. It will steal IMSI, manufacture and model info. It can also send SMS messages, delete SMS messages from inbox and dial phone numbers.
These five mobile malware threats are just the tip of the iceberg. New types of mobile malware are designed everyday by ill-intentioned individuals, and hardware-based security is just a temporary Band-Aid to defend against sophisticated mobile threats. Staying aware of what is out there and abreast of the latest threats is the first step in protecting yourself, but a joint effort is necessary and carriers will soon need to start arming their networks with security layers for their customers’ sake too.
Nominum is the worldwide leading provider of integrated subscriber, network and security solutions for network operators. Nominum is the provider of the N2 Platform that leverages more than 1 trillion DNS queries daily and enables the rapid development and seamless integration of applications that leverage DNS data. These applications are generated by the Nominum IDEAL ecosystem, an open ecosystem of application providers. The combined value of the N2 Platform and the IDEAL ecosystem provides network operators with the ability to deliver a differentiated subscriber experience with cost efficiency and agility. Nominum is a global organization headquartered in Redwood City, Calif.
Best Microsoft MCTS Certification,
Microsoft MCITP Training at certkingdom.com